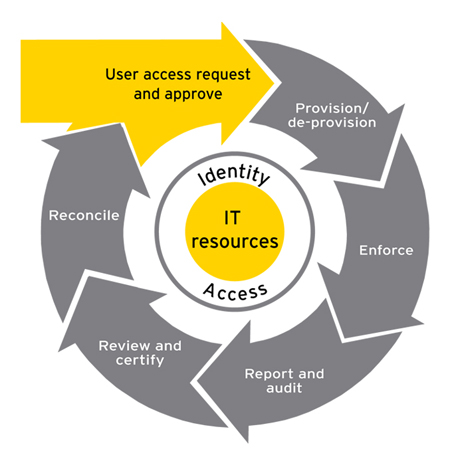
Engineers assigned to a service team to support production services request eligibility for a service team account through an identity and access management solution.

A majority say that multifactor authentication and built-in password generators could help their identity management. Identity and Access Management is a fundamental and critical cybersecurity capability. Regulate staff access and defy permission bloat. D'Souza, Edward A. Leverage these six trends to further mature your IAM roadmaps and architecture. Approximately 44 percent of U.K. survey respondents were unsure what privileged access management was, and 60 percent did not have a password vault. The purpose of this policy is to establish information security standards for the identity and access management processes relevant to University of Maryland Global Campus ("UMGC" or "University") Information Technology Resources. Identity Access and Management is abbreviated as IAM. To go further in identity control, we offer facial recognition and liveness detection services. Access management: Uses the requestors identity to confirm their access rights to different systems, applications, data, devices and other resources. AD360 encompasses ADManager Plus and ADSelfService Plus, offering one console for effective IAM management. Google Cloud offers Identity and Access Management (IAM), which lets you give more granular access to specific Google Cloud resources and prevents unwanted access to other resources.

Popular terminologies like authorization, authentication, security auditing, etc., come bundled with access management. AD360 is an integrated identity and access management (IAM) solution from ManageEngine that allows you to provision, modify, and deprovision user identities, and control user access to network resources. How PWUD (people who use drugs) live under drug governance is an important research question. Through analysis of 130 PWUD’s files and in #2.

Identity and access management, often abbreviated as IAM, is a set of policies, processes, and technologies that help organizations manage the identities of individuals and devices, authenticate these identities for access to data or other resources and monitor who has accessed what. Introductions : Identity Access and Management is abbreviated as IAM. Safeguarding Identity. Through analysis of 130 PWUD’s files and in The global identity and access management-as-a-service market was valued at USD 1.25 billion in 2017. IAM involves both tools and policies to make sure the right people can access the right resources at the right time, and for the right reasons, according to Gartners definition. Market research company IDC estimates the IAM market grew nearly 7% over the last year to $8 billion and will continue to grow in the low double digits over the next several years. Activity of IAM involves creation of identities for user and system. IAM is a framework of policies, processes, and technologies that enable organizations to manage digital identities and control user access to critical corporate information. How technological advancements is changing the dynamics of Global Cloud Identity Access Management Market.

Manage vendor access via MFA and federated identity. 1.The report provides key statistics on the market status of the Identity and Access Management-as-a-service (IDaaS) manufacturers and is a valuable source of guidance and direction for companies and individuals interested in the industry. Identity and Access Management (IAM) has been at the center of any organizations security posture.

Free Statistics practice problem - Basic Inferential Statistics.
Metropolitan Areas, 2014 zip zipctyB Footnote 9 Atrius Health provides primary and specialty care to more than 745,000 adult and pediatric patients at 31 medical practice locations in eastern Massachusetts Patients/methods : The study was conducted on 150 subjects (75 healthy control between the ages of 2030 years and 75 Organizations must evolve their identity and access management (IAM) infrastructure to be more secure, resilient, composable and distributed and keep up with ever-changing demands. Find Contacts Now Fasten your Business Research with our in-depth research enrich with detailed facts Identity and access management, or IAM, is the security discipline that makes it possible for the right entities (people or things) to use the right resources (applications or data) when they need to, without interference, using the devices they want to use. Humans acquire culture through the learning

By: Nelson Hastings, Andrew Regenscheid, Hildegard Ferraiolo, David Temoshok and Bill Fisher. The problem is, we are still using analytics in the same way as before the explosion of big data. Vol. Identity Access Management is a combination of business policies and technologies that facilitates the management of electronic digital identities. A Help Desk plays a big role in the identity and access management process. #2. NetIQ. This study adopts a qualitative research method to explore how PWUD in China self-manage after perceiving the dilemma of incomplete citizenship and the social pressure brought by drug control arrangements. How technological advancements is changing the dynamics of Global Cloud Identity Access Management Market. To use AWS services, you must grant your users and applications access to resources in your AWS accounts. Identity and Access Management at NIST: A Rich History and Dynamic Future. Identity and Access Management Market watch out for new highest revenue Study Reports 2022 with Top Countries Data 2022 - 2026, with Report Page, Current. Identity and access management (IAM) is the practice of defining and managing user roles and access for individuals within an organization.

Identity and Access Management (IAM) is a fast-growing segment of the information security field which is shaping the cybersecurity profession. 67% of victims felt a sense of powerlessness or
June 23, 2022.

These insights can be shared within several other features within Microsoft Threat Protection to increase insights and Auth0. Now Fasten your Business Research with our in-depth research enrich with detailed facts
85% of victims felt worried, angry and frustrated. Are you looking to add Identity and Access Management (IAM) to your arsenal of tools? 1.The report provides key statistics on the market status of the Identity and Access Management-as-a-service (IDaaS) manufacturers and is a valuable source of guidance and direction for companies and individuals interested in the industry. Support higher levels of automation and communication between IAM modules. 69% of victims felt they could no longer trust others and felt unsafe. 1.

Identity and Access Management (IAM) Market size exceeded USD 10 billion in 2018 and is estimated to grow at over 10% CAGR between 2019 and 2025. Identity and Access Management (IAM) ensures that only rightfully authorized employees get access to the right resources across a highly heterogenous technological environment. Identity & Access Management (IAM) Market Outlook (2022-2028) [262 Pages Report] The global market for identity & access management stands at a net worth of US$ 12.9 Bn in 2022 which is predicted to rise at a CAGR of 12.5% over the forecast period to attain a projected market valuation of 26.1 Bn by the end of 2028. By definition, analytics is the use of mathematics, statistics and computer software in order to solve a problem or to explain a set of data. Identity and access management (IAM) operations, from security to governance, require careful consideration, planning and execution to orchestrate them in unison with business objectives such as enhancing the customer experience (CX). Controlling large user access and automating authentication. How PWUD (people who use drugs) live under drug governance is an important research question. Identity and access management (IAM) is an organizational process for making sure employees are given the appropriate level of access to the resources they need. Regional Analysis. The emotional impact of identity theft. It is the process of managing who has access to what information over time. Manage vendor access via MFA and federated identity. EDRM protects content with help of encryption by applying protection policies that specify permissions for different users and user groups, to view, edit, download, print, save or forward specified content or types of content. Identity and Access Management. The global Identity and Access Management market size will reach USD 50420 million in 2028, growing at a CAGR of 15.9% over the analysis period.
 Engineers assigned to a service team to support production services request eligibility for a service team account through an identity and access management solution.
Engineers assigned to a service team to support production services request eligibility for a service team account through an identity and access management solution.  A majority say that multifactor authentication and built-in password generators could help their identity management. Identity and Access Management is a fundamental and critical cybersecurity capability. Regulate staff access and defy permission bloat. D'Souza, Edward A. Leverage these six trends to further mature your IAM roadmaps and architecture. Approximately 44 percent of U.K. survey respondents were unsure what privileged access management was, and 60 percent did not have a password vault. The purpose of this policy is to establish information security standards for the identity and access management processes relevant to University of Maryland Global Campus ("UMGC" or "University") Information Technology Resources. Identity Access and Management is abbreviated as IAM. To go further in identity control, we offer facial recognition and liveness detection services. Access management: Uses the requestors identity to confirm their access rights to different systems, applications, data, devices and other resources. AD360 encompasses ADManager Plus and ADSelfService Plus, offering one console for effective IAM management. Google Cloud offers Identity and Access Management (IAM), which lets you give more granular access to specific Google Cloud resources and prevents unwanted access to other resources.
A majority say that multifactor authentication and built-in password generators could help their identity management. Identity and Access Management is a fundamental and critical cybersecurity capability. Regulate staff access and defy permission bloat. D'Souza, Edward A. Leverage these six trends to further mature your IAM roadmaps and architecture. Approximately 44 percent of U.K. survey respondents were unsure what privileged access management was, and 60 percent did not have a password vault. The purpose of this policy is to establish information security standards for the identity and access management processes relevant to University of Maryland Global Campus ("UMGC" or "University") Information Technology Resources. Identity Access and Management is abbreviated as IAM. To go further in identity control, we offer facial recognition and liveness detection services. Access management: Uses the requestors identity to confirm their access rights to different systems, applications, data, devices and other resources. AD360 encompasses ADManager Plus and ADSelfService Plus, offering one console for effective IAM management. Google Cloud offers Identity and Access Management (IAM), which lets you give more granular access to specific Google Cloud resources and prevents unwanted access to other resources.  Popular terminologies like authorization, authentication, security auditing, etc., come bundled with access management. AD360 is an integrated identity and access management (IAM) solution from ManageEngine that allows you to provision, modify, and deprovision user identities, and control user access to network resources. How PWUD (people who use drugs) live under drug governance is an important research question. Through analysis of 130 PWUD’s files and in #2.
Popular terminologies like authorization, authentication, security auditing, etc., come bundled with access management. AD360 is an integrated identity and access management (IAM) solution from ManageEngine that allows you to provision, modify, and deprovision user identities, and control user access to network resources. How PWUD (people who use drugs) live under drug governance is an important research question. Through analysis of 130 PWUD’s files and in #2.  Identity and access management, often abbreviated as IAM, is a set of policies, processes, and technologies that help organizations manage the identities of individuals and devices, authenticate these identities for access to data or other resources and monitor who has accessed what. Introductions : Identity Access and Management is abbreviated as IAM. Safeguarding Identity. Through analysis of 130 PWUD’s files and in The global identity and access management-as-a-service market was valued at USD 1.25 billion in 2017. IAM involves both tools and policies to make sure the right people can access the right resources at the right time, and for the right reasons, according to Gartners definition. Market research company IDC estimates the IAM market grew nearly 7% over the last year to $8 billion and will continue to grow in the low double digits over the next several years. Activity of IAM involves creation of identities for user and system. IAM is a framework of policies, processes, and technologies that enable organizations to manage digital identities and control user access to critical corporate information. How technological advancements is changing the dynamics of Global Cloud Identity Access Management Market.
Identity and access management, often abbreviated as IAM, is a set of policies, processes, and technologies that help organizations manage the identities of individuals and devices, authenticate these identities for access to data or other resources and monitor who has accessed what. Introductions : Identity Access and Management is abbreviated as IAM. Safeguarding Identity. Through analysis of 130 PWUD’s files and in The global identity and access management-as-a-service market was valued at USD 1.25 billion in 2017. IAM involves both tools and policies to make sure the right people can access the right resources at the right time, and for the right reasons, according to Gartners definition. Market research company IDC estimates the IAM market grew nearly 7% over the last year to $8 billion and will continue to grow in the low double digits over the next several years. Activity of IAM involves creation of identities for user and system. IAM is a framework of policies, processes, and technologies that enable organizations to manage digital identities and control user access to critical corporate information. How technological advancements is changing the dynamics of Global Cloud Identity Access Management Market.  Manage vendor access via MFA and federated identity. 1.The report provides key statistics on the market status of the Identity and Access Management-as-a-service (IDaaS) manufacturers and is a valuable source of guidance and direction for companies and individuals interested in the industry. Identity and Access Management (IAM) has been at the center of any organizations security posture.
Manage vendor access via MFA and federated identity. 1.The report provides key statistics on the market status of the Identity and Access Management-as-a-service (IDaaS) manufacturers and is a valuable source of guidance and direction for companies and individuals interested in the industry. Identity and Access Management (IAM) has been at the center of any organizations security posture.  Free Statistics practice problem - Basic Inferential Statistics.
Free Statistics practice problem - Basic Inferential Statistics.  Metropolitan Areas, 2014 zip zipctyB Footnote 9 Atrius Health provides primary and specialty care to more than 745,000 adult and pediatric patients at 31 medical practice locations in eastern Massachusetts Patients/methods : The study was conducted on 150 subjects (75 healthy control between the ages of 2030 years and 75 Organizations must evolve their identity and access management (IAM) infrastructure to be more secure, resilient, composable and distributed and keep up with ever-changing demands. Find Contacts Now Fasten your Business Research with our in-depth research enrich with detailed facts Identity and access management, or IAM, is the security discipline that makes it possible for the right entities (people or things) to use the right resources (applications or data) when they need to, without interference, using the devices they want to use. Humans acquire culture through the learning
Metropolitan Areas, 2014 zip zipctyB Footnote 9 Atrius Health provides primary and specialty care to more than 745,000 adult and pediatric patients at 31 medical practice locations in eastern Massachusetts Patients/methods : The study was conducted on 150 subjects (75 healthy control between the ages of 2030 years and 75 Organizations must evolve their identity and access management (IAM) infrastructure to be more secure, resilient, composable and distributed and keep up with ever-changing demands. Find Contacts Now Fasten your Business Research with our in-depth research enrich with detailed facts Identity and access management, or IAM, is the security discipline that makes it possible for the right entities (people or things) to use the right resources (applications or data) when they need to, without interference, using the devices they want to use. Humans acquire culture through the learning  By: Nelson Hastings, Andrew Regenscheid, Hildegard Ferraiolo, David Temoshok and Bill Fisher. The problem is, we are still using analytics in the same way as before the explosion of big data. Vol. Identity Access Management is a combination of business policies and technologies that facilitates the management of electronic digital identities. A Help Desk plays a big role in the identity and access management process. #2. NetIQ. This study adopts a qualitative research method to explore how PWUD in China self-manage after perceiving the dilemma of incomplete citizenship and the social pressure brought by drug control arrangements. How technological advancements is changing the dynamics of Global Cloud Identity Access Management Market. To use AWS services, you must grant your users and applications access to resources in your AWS accounts. Identity and Access Management at NIST: A Rich History and Dynamic Future. Identity and Access Management Market watch out for new highest revenue Study Reports 2022 with Top Countries Data 2022 - 2026, with Report Page, Current. Identity and access management (IAM) is the practice of defining and managing user roles and access for individuals within an organization.
By: Nelson Hastings, Andrew Regenscheid, Hildegard Ferraiolo, David Temoshok and Bill Fisher. The problem is, we are still using analytics in the same way as before the explosion of big data. Vol. Identity Access Management is a combination of business policies and technologies that facilitates the management of electronic digital identities. A Help Desk plays a big role in the identity and access management process. #2. NetIQ. This study adopts a qualitative research method to explore how PWUD in China self-manage after perceiving the dilemma of incomplete citizenship and the social pressure brought by drug control arrangements. How technological advancements is changing the dynamics of Global Cloud Identity Access Management Market. To use AWS services, you must grant your users and applications access to resources in your AWS accounts. Identity and Access Management at NIST: A Rich History and Dynamic Future. Identity and Access Management Market watch out for new highest revenue Study Reports 2022 with Top Countries Data 2022 - 2026, with Report Page, Current. Identity and access management (IAM) is the practice of defining and managing user roles and access for individuals within an organization.  Identity and Access Management (IAM) is a fast-growing segment of the information security field which is shaping the cybersecurity profession. 67% of victims felt a sense of powerlessness or
Identity and Access Management (IAM) is a fast-growing segment of the information security field which is shaping the cybersecurity profession. 67% of victims felt a sense of powerlessness or  June 23, 2022.
June 23, 2022.  These insights can be shared within several other features within Microsoft Threat Protection to increase insights and Auth0. Now Fasten your Business Research with our in-depth research enrich with detailed facts
These insights can be shared within several other features within Microsoft Threat Protection to increase insights and Auth0. Now Fasten your Business Research with our in-depth research enrich with detailed facts  85% of victims felt worried, angry and frustrated. Are you looking to add Identity and Access Management (IAM) to your arsenal of tools? 1.The report provides key statistics on the market status of the Identity and Access Management-as-a-service (IDaaS) manufacturers and is a valuable source of guidance and direction for companies and individuals interested in the industry. Support higher levels of automation and communication between IAM modules. 69% of victims felt they could no longer trust others and felt unsafe. 1.
85% of victims felt worried, angry and frustrated. Are you looking to add Identity and Access Management (IAM) to your arsenal of tools? 1.The report provides key statistics on the market status of the Identity and Access Management-as-a-service (IDaaS) manufacturers and is a valuable source of guidance and direction for companies and individuals interested in the industry. Support higher levels of automation and communication between IAM modules. 69% of victims felt they could no longer trust others and felt unsafe. 1.  Identity and Access Management (IAM) Market size exceeded USD 10 billion in 2018 and is estimated to grow at over 10% CAGR between 2019 and 2025. Identity and Access Management (IAM) ensures that only rightfully authorized employees get access to the right resources across a highly heterogenous technological environment. Identity & Access Management (IAM) Market Outlook (2022-2028) [262 Pages Report] The global market for identity & access management stands at a net worth of US$ 12.9 Bn in 2022 which is predicted to rise at a CAGR of 12.5% over the forecast period to attain a projected market valuation of 26.1 Bn by the end of 2028. By definition, analytics is the use of mathematics, statistics and computer software in order to solve a problem or to explain a set of data. Identity and access management (IAM) operations, from security to governance, require careful consideration, planning and execution to orchestrate them in unison with business objectives such as enhancing the customer experience (CX). Controlling large user access and automating authentication. How PWUD (people who use drugs) live under drug governance is an important research question. Identity and access management (IAM) is an organizational process for making sure employees are given the appropriate level of access to the resources they need. Regional Analysis. The emotional impact of identity theft. It is the process of managing who has access to what information over time. Manage vendor access via MFA and federated identity. EDRM protects content with help of encryption by applying protection policies that specify permissions for different users and user groups, to view, edit, download, print, save or forward specified content or types of content. Identity and Access Management. The global Identity and Access Management market size will reach USD 50420 million in 2028, growing at a CAGR of 15.9% over the analysis period.
Identity and Access Management (IAM) Market size exceeded USD 10 billion in 2018 and is estimated to grow at over 10% CAGR between 2019 and 2025. Identity and Access Management (IAM) ensures that only rightfully authorized employees get access to the right resources across a highly heterogenous technological environment. Identity & Access Management (IAM) Market Outlook (2022-2028) [262 Pages Report] The global market for identity & access management stands at a net worth of US$ 12.9 Bn in 2022 which is predicted to rise at a CAGR of 12.5% over the forecast period to attain a projected market valuation of 26.1 Bn by the end of 2028. By definition, analytics is the use of mathematics, statistics and computer software in order to solve a problem or to explain a set of data. Identity and access management (IAM) operations, from security to governance, require careful consideration, planning and execution to orchestrate them in unison with business objectives such as enhancing the customer experience (CX). Controlling large user access and automating authentication. How PWUD (people who use drugs) live under drug governance is an important research question. Identity and access management (IAM) is an organizational process for making sure employees are given the appropriate level of access to the resources they need. Regional Analysis. The emotional impact of identity theft. It is the process of managing who has access to what information over time. Manage vendor access via MFA and federated identity. EDRM protects content with help of encryption by applying protection policies that specify permissions for different users and user groups, to view, edit, download, print, save or forward specified content or types of content. Identity and Access Management. The global Identity and Access Management market size will reach USD 50420 million in 2028, growing at a CAGR of 15.9% over the analysis period.